Small businesses tend to overlook cybersecurity. However, it’s important to understand that a cyber attack or data breach can be detrimental to your business. Below are some top cybersecurity best practices to follow:
- Don’t Share or Reuse Passwords
- Avoid Suspicious Emails, Links, and Pop-Ups
- Install Anti-Malware Software
- Use a Firewall
- Enable Multi-Factor Authentication
- Keep Hardware and Software Updated
- Limit Employee Access and Permissions
- Connect to Secure Wifi
Let’s begin.
Don’t Share or Reuse Passwords
Password management is crucial when protecting your business. It’s easy to just share passwords, but here are a few reasons why you should not:
- Accountability is gone. You won’t know who did what is everyone logs in under the same username and password.
- Liability is increased. Someone can use your credentials for unauthorized actions.
- You can give someone more privileges than they need. We discuss this more later on.
If you reuse passwords, sharing one password with someone can grant them access to other accounts. Even if you don’t voluntarily share this information, an attacker could compromise your repeated password and all associated accounts.
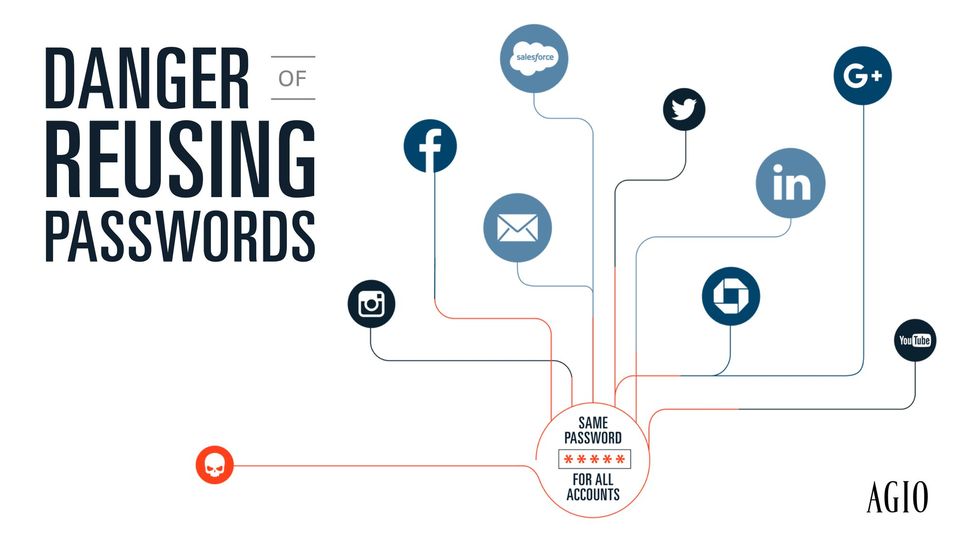
To avoid password repetition, use a secure password manager, like 1Password. These apps can generate secure ones for you, so you won’t have to remember any of them.
Avoid Suspicious Emails, Links, and Pop-Ups
Spam is inevitable. You’ll likely receive phishing emails or visit a site with malicious pop-ups. To protect your business, you and your staff must learn to recognize and avoid spam.
The most hands-off approach is security awareness training. Your employees can have interactive training with simulated campaigns. Reports are provided to track the effectiveness of training.
On the other hand, you can inform employees of red flags. Suspicious pop-ups, links, and attachments should never be clicked or downloaded. If it’s malicious, it could be anything from ransomware to more spam.

Suspicious emails, such as phishing emails, should be reported and examined by your IT department. If it is someone you know, go to the sender directly via phone or in-person. Their email may have been compromised.
Install Anti-Malware Software
Most anti-malware software is affordable. The costs associated with a breach or attack far outweigh the software costs. While it can’t prevent everything, having at least some protection is better than none. If you have a Windows machine, you can use Windows Security.
The right software will depend on your budget and needs. Your IT team should discuss your options with you.
Building a successful business takes time. Protect it by protecting your IT systems from malware.
Use a Firewall
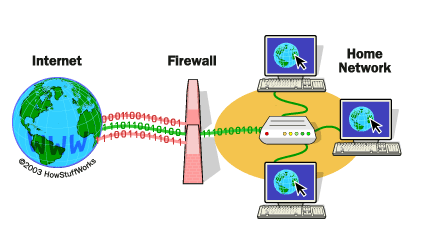
A firewall is hardware, software, or both. It’s a device that monitors all traffic and decides to allow or block it based on specific security rules that vary by organization. Essentially, it filters traffic.
The goal of a firewall is to protect your internal network from external sources (the internet). It can block malicious or unwanted traffic, such as malware. For basic protection for your business, it’s important to have one. While anti-malware software protects your files from unwanted programs, a firewall will block the malicious traffic altogether.
Firewalls should be configured by your IT department. Without proper settings and configurations, the firewall cannot do its job. Cost varies, but for most small businesses, an advanced or enterprise firewall is not needed. Your IT team can work with your specific needs.
Enable Multi-Factor Authentication
Multi-factor authentication (MFA) is an identity verification method. It’s an extra layer of security to your accounts because you will need more than just a password to login.
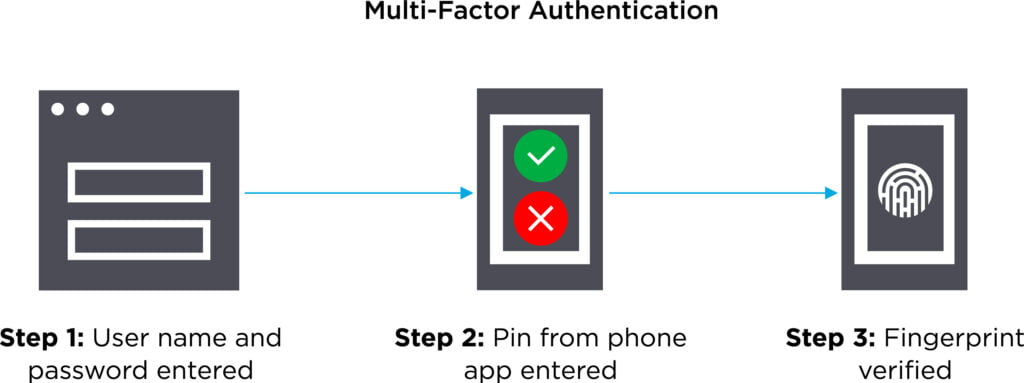
Multi-factor authentication is available for most apps and websites. If possible, you should enable it through an authenticator app, such as Google Authenticator or Microsoft Authenticator.
Enabling MFA on critical IT systems can enhance the security of your business by preventing unauthorized access.
Keep Hardware and Software Updated
New updates can include things like bug fixes and usability improvements, but also important security patches. When a security update is released, update as soon as possible. Vulnerabilities are present and exploited in older versions of software, so your business and data are more at risk.
In addition to boosting security, updates also improve performance, add new features, or offer better compatibility with more devices and applications.
Limit Employee Access and Permissions
An important concept in cybersecurity is called the principle of least privilege. It says users, systems, and processes only have access to resources that are needed. Resources include networks, files, and systems. An example would be giving users, like you and your employees, restricted accounts while the IT staff gets administrator accounts.
Allowing employees to access resources they do not need increases your risk of exploitation, deletion, modification, or theft. Many attackers need admin privileges to execute malware. Sometimes, malicious hackers will go through multiple users and systems until they reach their target. With least privilege, the hacker will be blocked from doing so.
Least privilege is even more important for administrative and senior level job functions, as they usually have more permissions and access. You should discuss with your IT department about implementing this.
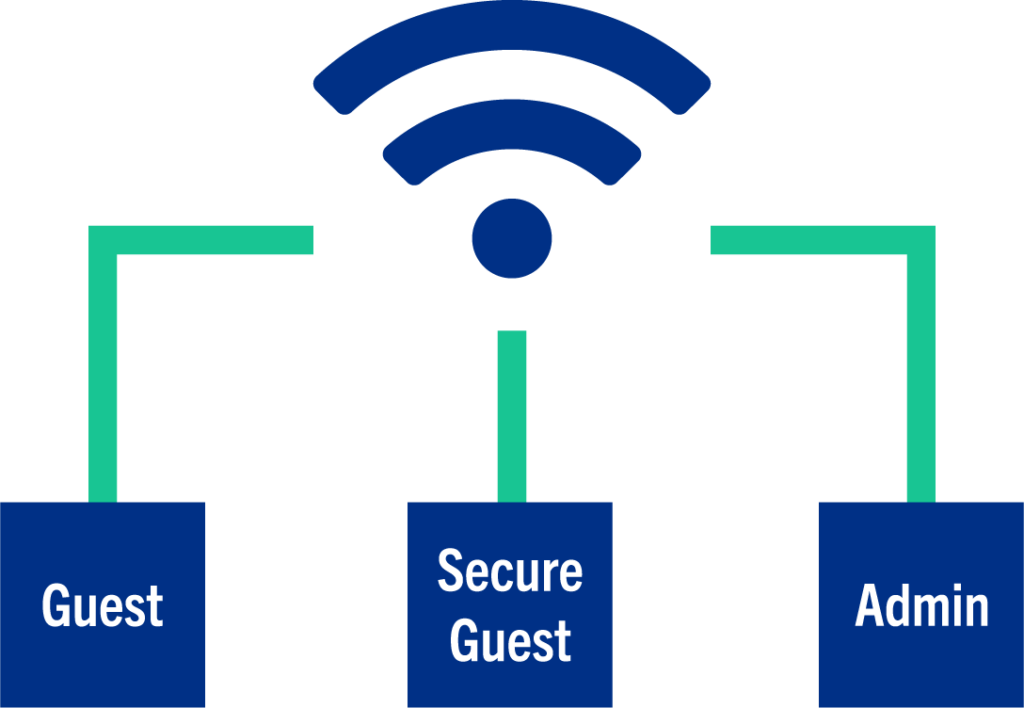
Connect to Secure Wifi
Your office network should not be open. You’ll want to secure it. Here’s a few ways how:
- Password protect your network. Change the default password, if there is one.
- Segment your network. Make one for staff and another for guests.
- Do not allow untrusted devices on your secure network.
Your IT team should be able to assist with this. However, you’ll want your staff to understand they cannot connect personal devices to the trusted network. This can put your organization at risk because the activity is not monitored.
When working out of the office, you’ll want to make sure you or any employees do not connect to public wifi. Usually, it’s open or has weak security that can expose you to malicious traffic or attackers.
Next Steps
If you have one, reach out to your IT department to ensure you are following cybersecurity best practices for your small business. Remember, cyber attacks are not just happening to larger organizations.
If you have any questions or comments, feel free to contact us.



