When it comes to cybersecurity, you’re the first line of defense. Unfortunately, there are many ways you could be putting yourself at risk, but you can do several things right now to stay safe.
We’re going to give you 8 tips on how to protect yourself online.
Here’s a rundown:
- Strengthen Your Passwords
- Avoid Interacting with Suspicious Emails
- Don’t Reuse Passwords
- Activate Anti-Virus
- Use Multi-Factor Authentication
- Stop Using Public Wi-Fi
- Don’t Share Your Passwords
- Keep Your Devices Updated
Let’s get into it.
1. Strengthen Your Passwords
Your password is the most important key to your sensitive data. When it comes to hacking, there are many methods a bad guy can use, but it all boils down to the strength of your passwords (plus some other things we’ll discuss later). These are the Top 10 Most Used and Exposed Passwords:
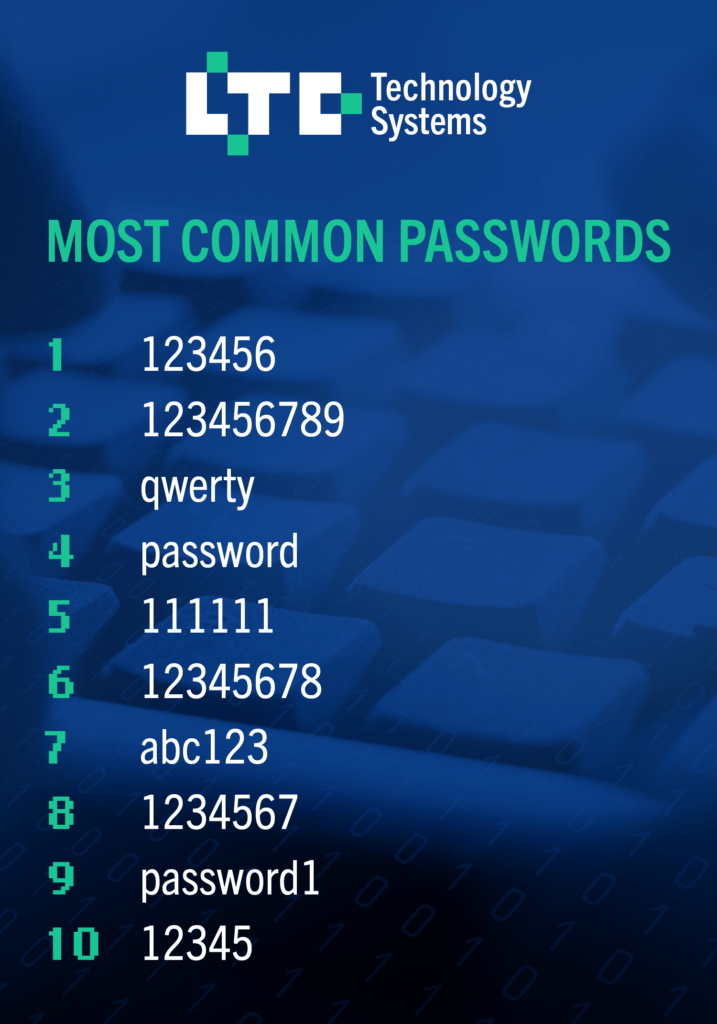
Passwords like these can be cracked in no time at all. For example, a bad actor could use a brute force attack. This refers to a number of different attacks they perform to find credentials.
Essentially the computer and software do all the work for them while they sit back and wait for a hit. The time it takes will vary on the hacker’s machine, knowledge, and your password strength.
However, it doesn’t have to be a shot in the dark. If they know enough about you, they might figure it out themselves. Check out Tip #3 for more information.
Clearly, an unknown person with your information is going to end up bad. Plus, the dark web is full of personal information that is sold by hackers. When someone purchases your login, who knows what could happen. Bad guys can even run stolen credentials to see if they are still active.
That’s why it’s important to choose a long password with multiple elements.
Here’s some guidelines:
- Upper and lowercase numbers
- Numbers
- Symbols
- Nonsense words and phrases
- Memorable to you, but no identifying information
- 12+ characters
Sometimes it can difficult to remember such long passwords. We recommend purchasing a password manager. This way, your information is only accessible to you and you’re staying safe online.
2. Avoid Interacting with Suspicious Emails
While your email provider will block most spam, sometimes phishing emails slip through the cracks. You may be more trusting of an email from large companies such as Amazon and Google, but if these emails are unsolicited, grammatically incorrect, or requesting sensitive information, you’re better off ignoring them.
Here’s an example of an email you might receive:
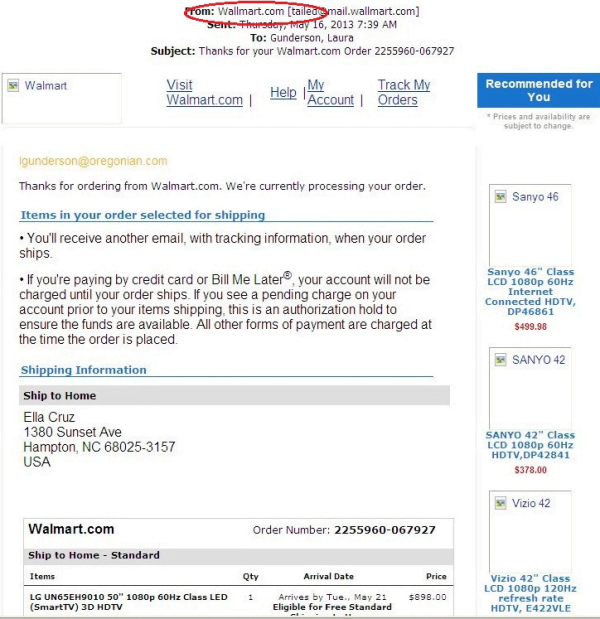
While some traditional signs of a phishing email are still important, many phishing attempts have evolved. You can still look out for the telltale signs:
- Spelling or grammatical errors: Sometimes there will be incorrect or missing punctuation, misspelled words, or wrong words. For example, they meant its but typed it’s. In the image above, we can see they spelled “Walmart” as “Wallmart” – a clear sign that this email is spam.
- Odd phrasing: The senders of phishing emails don’t really care about sounding professional. They use social engineering tactics to distract you from their untrustworthy email. This results in emails with mixed up words or phrases that just don’t make sense.
- Threats: Phishing emails come to you with a sense of urgency. They mostly make claims such as “Your account is suspended. Reset your password” or “There was a problem with your payment. Resubmit now” or something along those lines.
- Phony email address: Check the email address. Many bad guys have learned to mask the true address, but many still don’t. If it’s supposed to be an email from Amazon, but you see “hr@hy-drop.com” then it’s not something you should trust. Some might be from “order-update@amazon.com”. If you order often, you’d be right to feel suspicious. In the example above, we can see the incorrect email address with “wallmart” in it.
- Unsecure redirection or attachment: Phishing emails are designed to make you click on something. This can be an attachment or link. Avoid clicking on anything – a URL can be masked and an attachment can contain malware that activates as soon as a download is complete.
Secure your digital safety by going straight to the source instead of a link or attachment in a strange email.
3. Don’t Reuse Passwords
In addition to weak passwords, you shouldn’t use the same passwords.
You may use the same (or very similar) passwords for everything. Once a bad guy figures this out, he can easily gain access to your accounts and information.
Let’s say you have a very strong password you created after reading the tips above. Again, you use this password for everything. If a hacker gets ahold of it, your accounts are now at risk.
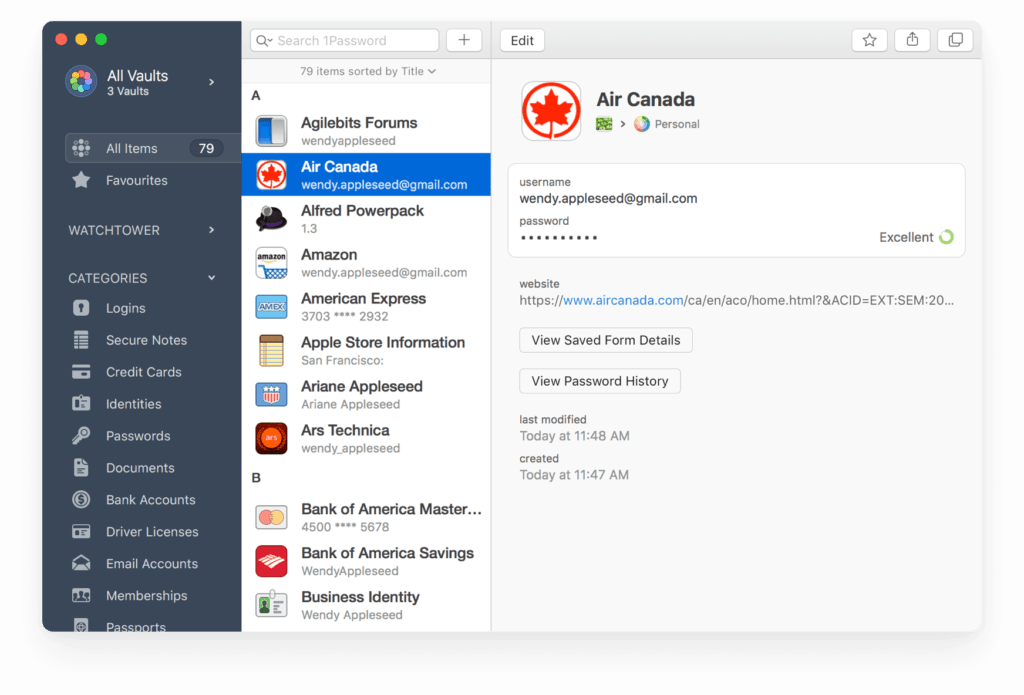
For the best cybersecurity practice, it’s best for each platform to have its own unique password. As mentioned before, you can use a password manager, like 1Password. This will help you keep track of each platform’s login while keeping everything safe.
4. Activate Anti-Virus
Anti-virus software is a simple, hands-off approach to detecting and removing malware. If you use the most common operating system, Windows, you can activate Microsoft’s built-in software: Windows Defender. If you want to explore other anti-virus options, there are many popular choices depending on your needs.
We recommend running frequent checks depending on your usage. This will range from once a week to once a day. Your anti-virus software will ensure any problems are found and solved quickly, allowing you to stay safe while you’re online.
5. Use Multi-Factor Authentication
Typically, when you make an account online, you have the option of adding your phone number, security questions, or some other form of communication. This is for your protection. If there is an unusual log in, the service provider may ask a security question or send a code to your cell phone. This is called multi-factor authentication, or MFA for short.
If a bad guy does have the correct password, he will not be able to access your account. Multi-factor authentication will prevent that.
According to research done by Google, adding a recovery phone number to your Google Account can block up to 100% of automated bots, 99% of bulk phishing attacks, and 66% of targeted attacks.
Microsoft also encourages multi-factor authentication. For Microsoft accounts, adding MFA can block over 99.9% of account compromise attacks.
If you haven’t already, go ahead and add multi-factor authentication to your accounts for advanced online protection.
6. Stop Using Public Wi-Fi
Many people think connecting to public wi-fi networks would be harmless. That couldn’t be further from the truth.
If you’re on an open network – or even one with a simple password to access – you will never know who is connected to it. This person could use the network to gain access to your device.
We recommend doing either of these options:
- Use a secure VPN
- Use a secure hotspot
A VPN will essentially hide your activity from anyone else on the network. It’s like your own secret tunnel. Most people use them for public networks, but you can use them on your home network as well.

A hotspot is a portable Wi-Fi access point. This can come in the form as a small device or even your mobile phone. When you have a hotspot with a connection, you’ll have secure access to the Internet. Some examples of secure hotspots include Apple iPhone’s mobile hotspot and prepaid mobile hotspots (like the one pictured) that you purchase at major retailers.
In conclusion, avoid connecting to public networks. If you must, use a VPN. Remember to never shop online or input sensitive information while on a public network. Using a mobile hotspot will bypass these concerns altogether.
7. Don’t Share Your Passwords
Sharing your passwords, virtually or face-to-face, could put your information in the wrong hands. No matter how much you trust the person, they may use this password on an unsecure network or infected device. They could seek revenge and do something malicious. Perhaps they will share it with another person that you won’t know about.
If you do this in a professional setting, there is even a higher risk. In a recent report, 2 out of 3 (69%) employees share passwords.

There are many reasons why this is dangerous.
Your colleague may be using an unsecured device. Not to mention, they can mistakes using your credentials that could get you in lots of trouble. If a bad guy gets access to your network, shared passwords will make his job much easier.
To protect yourself, avoid sharing your passwords with anyone.
8. Keep Your Devices Updated
Many people ignore or delay software updates. However, the updates can have important security updates that are critical for cybersecurity.
Sometimes, there might be holes in software that expose security vulnerabilities. Threat actors love an easy way in, so they will take advantage of it. Those who have outdated software become the victims of these exploits.
It’s best to keep all your devices up-to-date so you’re always safe online.
Plus, your experience with be enhanced with new features and improved usability. So why not do it? Dedicating some time to update your device could save you trouble later on.
Make sure to keep your computer, mobile devices, and applications updated.
So what now?
Our security tips should give you the upper hand when it comes to cybersecurity, so be sure to follow them so you can secure yourself online.
Remember to:
- Use strong, individual passwords for everything and do not share them
- Use multi-factor authentication and anti-virus software
- Avoid public wi-fi
- Ignore suspicious emails
Have any questions or comments? Send a message to let us know.


